FIND UNIQUE NANO TECHNOLOGY
Nano technology referred to the particular technological goal of precisely manipulating atoms and molecules for fabrication of macro scale products, also now referred to as molecular nanotechnology which defines nanotechnology as the manipulation of matter with at least one dimension sized from 1 to 100 nano meters.
Sunday, December 31, 2017
Monday, December 18, 2017
Friday, December 8, 2017
Friday, December 9, 2016
10 Best Hackers The World Has Ever Known
In the world of web where we get the global connectivity, it is far
easier to break into someone’s personal zone. By personal, we do not just mean
the social media. The world wide web which has become the hub of storing and
restoring information, considered to be the safest vault, is a mere toy in the
hands of a few computer geniuses. Hackers, Black Hat Hackers, villains,
crackers, cyber-criminals, cyber pirates as they are well-known, throw a
malicious software or virus at a system to gain the access to the desired
information. Piqued by curiosity, they may perhaps break into your system too.
Here are top 10 hackers or the whiz kids who put the world in awe with their
dexterity.
1.
Gary McKinnon
Gary McKinnon
must’ve been a curious, restless child, for to gain information on UFOs, he
thought it better to get a direct access into the channels of NASA. He
infiltrated 97 US military and NASA computers, by installing virus and deleting
a few files. All the efforts to satisfy his curiosity, but, alas, curiosity
killed the cat. It was soon found that McKinnon was guilty of having hacked the
military and NASA websites from his girlfriend’s aunt’s house in London. While
entering and deleting the files from these websites wasn’t enough, McKinnon
thought of shaming the security forces by putting out a notice on the website
that said, “Your security is crap.” Well, looks like McKinnon was something, if
he could shut down the US Military’s Washington Network of about 2000 computers
for 24 hours, making the hack, the biggest military computer hack of all time!
2. LulzSec
LulzSec or Lulz Security, a high profile, Black Hat hacker group,
gained credentials for hacking into Sony, News International, CIA, FBI,
Scotland Yard, and several noteworthy accounts. So notorious was the group that
when it hacked into News Corporations account, they put across a false report
of Rupert Murdoch having passed away. While the group claims to have retired
from their vile duties, the motto of the group, “Laughing at your security
since 2011!” stays alive. There are assertions of the group having hacked into
the websites of the newspapers like The Times and The Sun to post its retirement news. Many,
however, claim that this group had taken it upon itself to create awareness
about the absence of efficient security against hackers.
3.Adrian Lamo
Adrian Lamo decided to switch careers when he realized the
potentials of his skills. He became a news when he hacked into Yahoo!,
Microsoft, Google, and The New York Times. This, although culminated into his
arrest, it later helped him gain the batch of an American Threat Analyst. A guy
who would hack into top-notch accounts sitting in the spacious and comforting
cafeterias, libraries, internet cafes, soon turned Wikileaks suspect Bradley
Manning over to FBI. While Manning was arrested for leaking several hundred
sensitive US government documents, Lamo went hiding or should we presume,
undercover?
4. Mathew Bevan and Richard Pryce
5. Jonathan James
The first juvenile
to be imprisoned for a cyber-crime at the age of 16, Jonathan James or better
known as c0mrade, hacked into Defense Threat Reduction Agency of US department.
Further, he installed a sniffer that scrutinized the messages passed on between
the DTRA employees. Not only did he keep a check on the messages being passed
around, in the process, he collected the passwords and usernames and other such
vital details of the employees, and further even stole essential software. All
this cost NASA to shut down its system and to pay from its pocket $41,000.
c0mrade, however, had a bitter ending as James committed suicide in 2008.
6. Kevin Poulsen
How far would you go to win your dream car or a dream house? How
far will you go to win an online contest or a radio show contest? Perhaps, you
shall keep trying your luck, unless you are Kevin Poulsen! Poulsen infiltrated
a radio shows call-in contest just so he could win a Porsche. Dark Dante, as he
was better known, went underground after FBI started pursuing him. He, later,
was found guilty of seven counts of mail, wire and computer fraud, money
laundering and the likes. What turned out to be rewarding in Dark Dante’s case
is – his past crafted his future. Poulsen now serves as a Senior Editor at
Wired.
7. Kevin Mitnick
Clad in an Armani
suit, when a bespectacled face in his mid-40s smiles at you from the computer
screen, you can hardly consider the man a cyber-criminal. Such is the case with
Kevin David Mitnick. Once upon a time, the most wanted cyber-criminal of US,
now is an affluent entrepreneur. Kevin, who is now a security consultant, was
convicted of hacking Nokia, Motorola and Pentagon. He pleaded guilty to seven
counts of fraud that included wire fraud, computer fraud and of illegally
interception a wire communication. After five years of incarceration that
included eight months of solitary confinement, Mitnick now has started afresh.
However, his knack with the computers is still reminisced and was even depicted
on celluloid in the films Takedown and Freedom Downtown.
8. Anonymous
The concept of being
a “digital Robin Hood” was far from being conceived, but in the computer age,
it is very likely that someone somewhere has bagged this title. A “hacktivist
group” called Anonymous are known with the penname of being the “digital Robin
Hood” amongst its supporters. Identified in public by wearing a Guy Fawkes
Masks, Anons, as they are widely known, have publicized themselves by attacking
the government, religious and corporate websites. The Vatican, the FBI, the
CIA, PayPal, Sony, Mastercard, Visa, Chinese, Israeli, Tunisian, and Ugandan
governments have been amongst their targets. Although, Anons have been arguing
whether to engage in a serious activism or a mere entertainment, many of the
group members have clarified their intent which is to attack internet
censorship and control.
9. Astra
Astra, a Sanskrit
word for weapon was the penname of a hacker who dealt in the weapon stealing
and selling. A 58-year-old Greek Mathematician hacked into the systems of
France’s Dassault Group, stole vulnerable weapons technology data and sold it
to different countries for five long years. While the real identity of the
ASTRA remains untraced, officials have said that he had been wanted since 2002.
Astra sold the data to approximately 250 people from around the globe, which
cost Dassault $360 millions of damage.
10. Albert Gonzalez
How safe is internet
banking? When we browse through the profile of this mastermind, we are certain
that one ought to use the World Wide Web with immense care. For two long years,
Albert Gonzalez, stole from credit cards of the netizens. This was recorded to
be the biggest credit card theft in the history of mankind. He resold
approximately 170 million credit cards and ATM numbers. He did so by installing
a sniffer and sniffing out the computer data from internal corporate networks.
When arrested, Gonzalez was sentenced to 20 years in Federal prison.
video of 5 best hacker
video of 5 best hacker
Wednesday, November 30, 2016
TRANSFORMING INVENTIONS That Will Blow Your Mind
From Shape shifting Buildings, to Real Transforming Cars, here are 8 Transforming Inventions that will blow your mind…….
TRANSFORMING INVENTIONS VIDEO
Wednesday, November 23, 2016
BIO TECHNOLOGY
BIO TECHNOLOGY = At its simplest, biotechnology is technology based on biology - biotechnology harnesses cellular and biomolecular processes to develop technologies and products that help improve our lives and the health of our planet.Currently, there are more than 250 biotechnology health care products and vaccines available to patients, many for previously untreatable diseases. More than 13.3 million farmers around the world use agricultural biotechnology to increase yield.
WHAT IS BIO GASS =
Bio gas typically refers to a mixture of different gases produced by the breakdown of organic matter in the absence of oxygen. Bio gas can be produced from raw materials such as agricultural waste, manure, municipal waste, plant material, sewage, green waste or food waste
HOW TO MANUFACTURING BIO GASS=
Regardless of your design, avoid using biogas or any other fuel to heat your digester. Make sure energy you use is excess energy on its way to being wasted. Step 4. Neutral pH is an important parameter in anaerobic digestion, just as it is for aerobic composting
GENRAL USED BIO TECHNOLOGY =
- Generation of electricity and heat (CHP)
- Feeding biogas into the natural gas grid
- Use in the mobility sector
Sunday, November 13, 2016
HOLOGRAM TECHNOLOGY
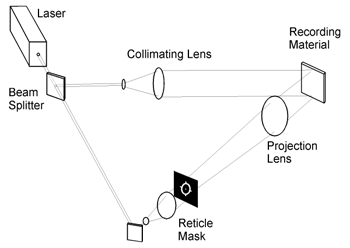
Holography is the science and practice of making holograms. Typically, a hologram is a photographic recording of a light filed, rather than of an image formed by a lens, and it is used to display a fully 3-D image of the holography subject, which is seen without the aid of special glass or other intermediate optics.
The hologram itself is not an image and it is usually unintelligible when viewed under diffuse reflection light. It is an encoding of the light field as an interface pattern of seemingly random variations in the opacity, density, or surface profile of the photographic medium. When suitably lit, the interference pattern diffraction the light into a reproduction of the original light field and the objects that were in it appear to still be there, exhibiting visual depth cues such as parallax and virtual that change realistically with any change in the relative position of the observer.
In its pure form, holography requires the use of laser light for illuminating the subject and for viewing the finished hologram. In a side-by-side comparison under optimal conditions, a holographic image is visually indistinguishable from the actual subject, if the hologram and the subject are lit just as they were at the time of recording. A microscopic level of detail throughout the recorded volume of space can be reproduced. In common practices, however, major image quality compromises are made to eliminate the need for laser illumination when viewing the hologram, and sometimes, to the extent possible, also when making it.
LASER : In laser holography, the hologram is recorded using a source of laser light, which is very pure in its color and orderly in its composition.
PHYSICS OF HOLOGRAPHY : For a better understanding of the process, it is necessary to understand optics and diffraction. Interference occurs when one or more wave front are superimposed. Diffraction occurs whenever a wave front encounters an object. The process of producing a holographic reconstruction is explained below purely in terms of interference and diffraction.
HOW IT WORK :Holography is a technique that enables a light field, which is generally the product of a light source scattered off objects, to be recorded and later reconstructed when the original light field is no longer present, due to the absence of the original objects. Holography can be thought of as somewhat similar to sound recording, whereby a sound field created by vibrating matter like musical instruments is encoded in such a way that it can be reproduced later, without the presence of the original
vibrating matter
Subscribe to:
Comments (Atom)


